What is NIST RMF?
The NIST Risk Management Framework (RMF) is a structured and systematic process designed to help organizations, including government agencies and private entities, manage and mitigate cybersecurity risks associated with their information systems. The framework was developed by the National Institute of Standards and Technology (NIST), which is a non-regulatory agency of the United States Department of Commerce.
The NIST RMF provides a set of guidelines, standards, and processes for managing information security and risk at the organizational level. The framework emphasizes a risk-based approach to cybersecurity, encouraging organizations to assess and prioritize risks based on their potential impact on the organization's mission and objectives.
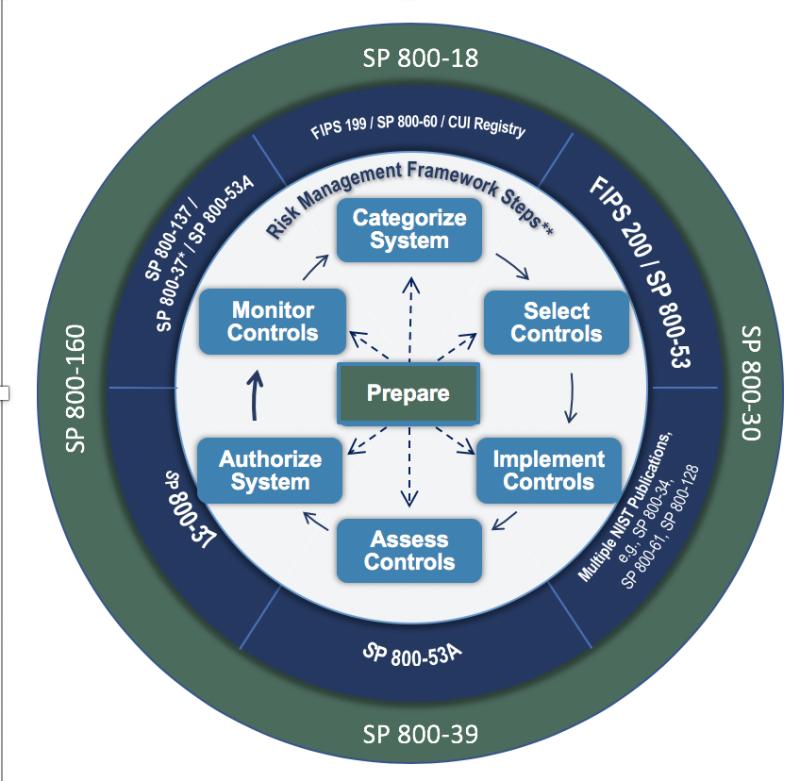
The key steps in the NIST RMF process are:
Prepare:
- Establish the context and priorities for the risk management process.
- Develop and document the organization's risk management strategy.
Categorize:
- Identify and classify information systems and the information processed within them.
- Define the impact levels associated with the confidentiality, integrity, and availability of the information.
Select:
- Choose appropriate security controls to safeguard the information system based on the determined impact levels.
- Tailor the controls to meet the organization's specific needs and circumstances.
Implement:
- Put the selected security controls into practice within the information system.
- Document the implementation of controls and ensure they are operating effectively.
Assess:
- Evaluate the security controls to ensure they are implemented correctly and are effective in managing risk.
- Conduct security assessments and continuous monitoring activities.
Authorize:
- Review the security documentation and assessment results.
- Make a risk-based decision on whether to authorize the information system to operate.
Monitor:
- Continuously monitor security controls and the overall security posture of the information system.
- Report and respond to security incidents and changes in the risk environment.
The NIST RMF is applicable to a wide range of organizations, including federal agencies, contractors, and private-sector entities that handle sensitive information. It provides a systematic and flexible approach to managing cybersecurity risks, and it aligns with other cybersecurity frameworks and standards.
It's worth noting that the NIST RMF has evolved over time, and the latest version (as of my knowledge cutoff in January 2022) is outlined in NIST Special Publication 800-37, Revision 2: "Risk Management Framework for Information Systems and Organizations: A System Life Cycle Approach for Security and Privacy." Organizations are encouraged to refer to the latest NIST publications for the most up-to-date guidance on implementing the RMF.
Unraveling risk management: What is NIST RMF?
The National Institute of Standards and Technology (NIST) Risk Management Framework (RMF) is a comprehensive, flexible, repeatable, and measurable process that organizations can use to manage information security and privacy risk. The RMF is a framework, not a set of requirements. It provides a process and a set of tools that organizations can use to tailor a risk management program to their specific needs.
2. Understanding the NIST RMF and its application in cybersecurity
The NIST RMF is a risk-based approach to cybersecurity. It helps organizations to identify, assess, and mitigate the risks to their information systems and data. The RMF is also designed to help organizations to comply with applicable cybersecurity regulations.
The RMF consists of six steps:
- Prepare: The organization prepares for the RMF by developing a risk management plan and identifying the information systems and data that need to be protected.
- Categorize: The organization categorizes the information systems and data based on their impact on the organization's mission and operations.
- Select: The organization selects the security controls that will be implemented to protect the information systems and data.
- Implement: The organization implements the security controls and verifies that they are operating as intended.
- Assess: The organization assesses the effectiveness of the security controls and makes necessary adjustments.
- Monitor: The organization monitors the security controls and the information systems and data for changes that could impact risk.
Tips for implementing NIST RMF to assess and mitigate risks effectively
Here are some tips for implementing NIST RMF to assess and mitigate risks effectively:
- Involve stakeholders throughout the process. The RMF is a collaborative process that should involve stakeholders from all levels of the organization.
- Use a risk-based approach. The RMF is a risk-based approach to cybersecurity, so it is important to focus on the risks that are most important to the organization.
- Tailor the RMF to your organization's needs. The RMF is a framework, not a set of requirements. It is important to tailor the RMF to your organization's specific needs and resources.
- Monitor and update your RMF on a regular basis. The threat landscape is constantly changing, so it is important to monitor and update your RMF on a regular basis to ensure that it is still effective.
Here are some additional tips for implementing NIST RMF:
- Use a risk assessment tool. There are a number of risk assessment tools available that can help you to identify and assess the risks to your information systems and data.
- Use a security control catalog. A security control catalog is a list of security controls that can be used to mitigate the risks to information systems and data.
- Use a continuous monitoring tool. A continuous monitoring tool can help you to monitor your information systems and data for changes that could impact risk.
By following these tips, you can implement NIST RMF effectively and assess and mitigate risks to your organization's information systems and data.