What is NIST Cybersecurity Framework (CSF)?
The NIST Cybersecurity Framework (CSF) is a set of guidelines, standards, and best practices developed by the National Institute of Standards and Technology (NIST) to help organizations manage and improve their cybersecurity posture. It provides a flexible and voluntary framework that can be applied to various sectors and industries to enhance the overall cybersecurity resilience of an organization.
The NIST CSF was created in response to Executive Order 13636, which called for the development of a framework to improve the cybersecurity of critical infrastructure in the United States. The framework is designed to be adaptable to organizations of all sizes and types, providing a common language for expressing cybersecurity risk and management priorities.
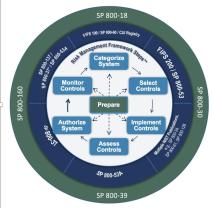
The NIST CSF consists of three main components:
1. Framework Core:
- The core is a set of cybersecurity activities, outcomes, and references that are common across critical infrastructure sectors. It is organized into five functions:
- Identify: Develop an understanding of the organization's cybersecurity risk posture.
- Protect: Implement safeguards to ensure the delivery of critical infrastructure services.
- Detect: Identify and respond to cybersecurity events.
- Respond: Take action to contain and mitigate the impact of a cybersecurity incident.
- Recover: Restore services affected by a cybersecurity incident.
2. Framework Implementation Tiers:
- The implementation tiers provide a way for organizations to characterize their approach to managing cybersecurity risk. There are four tiers:
- Partial (Tier 1): Organizations at this tier have an ad-hoc approach to cybersecurity.
- Risk Informed (Tier 2): Organizations are aware of cybersecurity risks and have established basic cybersecurity processes.
- Repeatable (Tier 3): Organizations have a formalized and repeatable process for managing cybersecurity risk.
- Adaptive (Tier 4): Organizations are continuously improving their cybersecurity practices based on lessons learned and predictive indicators.
3. Framework Profile:
- The profile is a customizable alignment of the framework core elements to an organization's business requirements, risk tolerance, and resources. It allows organizations to prioritize and focus on the specific cybersecurity outcomes and activities most relevant to their goals.
Organizations can use the NIST CSF to:
- Assess their current cybersecurity posture: Identify strengths, weaknesses, and areas for improvement.
- Establish or improve a cybersecurity program: Develop or enhance policies, processes, and controls.
- Communicate cybersecurity risk: Provide a common language for discussing cybersecurity risk management within the organization and with external stakeholders.
- Align with other cybersecurity standards: The NIST CSF can complement other cybersecurity standards and frameworks.
It's important to note that the NIST CSF is a voluntary framework, and organizations are encouraged to adapt it to their specific needs and risk environments. It is widely used by both private and public sector organizations as a foundational tool for cybersecurity risk management.
Strengthening cybersecurity: What is NIST Cybersecurity Framework (CSF)?
The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) is a voluntary framework that provides organizations with a common language and approach to managing cybersecurity risk. The CSF is based on existing standards, guidelines, and best practices, and it is designed to be flexible and adaptable to the needs of organizations of all sizes and industries.
The CSF is organized around five functions: Identify, Protect, Detect, Respond, and Recover. Each function contains a set of categories and subcategories that provide specific guidance on how to manage cybersecurity risk.
Understanding the principles and components of the NIST CSF for robust cybersecurity
The NIST CSF is based on the following principles:
- Risk-based approach: The CSF emphasizes the importance of taking a risk-based approach to cybersecurity. This means that organizations should focus on protecting their most critical assets and mitigating the risks that pose the greatest threat to those assets.
- Integration: The CSF is designed to be integrated with other cybersecurity frameworks and standards. This allows organizations to build on their existing cybersecurity programs and avoid duplicating efforts.
- Flexibility: The CSF is flexible and adaptable to the needs of organizations of all sizes and industries. Organizations can choose to implement the CSF in a way that is most effective for them.
The NIST CSF consists of the following components:
- Core: The Core of the CSF is a set of 23 high-level cybersecurity activities. The Core is applicable to all organizations, regardless of their size or industry.
- Implementation Tiers: The CSF defines three implementation tiers: Tier 1 (Partial), Tier 2 (Risk-Informed), and Tier 3 (Adaptive). Each tier represents a higher level of cybersecurity maturity.
- Framework Profile: The Framework Profile is a document that organizations can use to describe their cybersecurity program using the CSF.
Tips for implementing NIST CSF to enhance the security posture of an organization
Here are some tips for implementing NIST CSF to enhance the security posture of an organization:
- Start by assessing your current cybersecurity program. This will help you to identify the gaps between your current program and the CSF.
- Develop a CSF implementation plan. This plan should include specific goals, objectives, and timelines for implementation.
- Implement the CSF in a phased approach. Start with the Core activities and then move on to the Implementation Tiers.
- Monitor and update your CSF implementation on a regular basis. The cybersecurity threat landscape is constantly changing, so it is important to keep your CSF implementation up to date.
Here are some additional tips for implementing NIST CSF:
- Involve stakeholders throughout the process. The CSF implementation process should involve stakeholders from all levels of the organization.
- Use NIST CSF resources. NIST provides a number of resources to help organizations implement the CSF, including a Framework Profile template and a CSF implementation guide.
- Get help from a qualified professional. If you need help implementing the CSF, there are a number of qualified professionals who can assist you.
By following these tips, you can implement NIST CSF effectively and enhance the security posture of your organization.