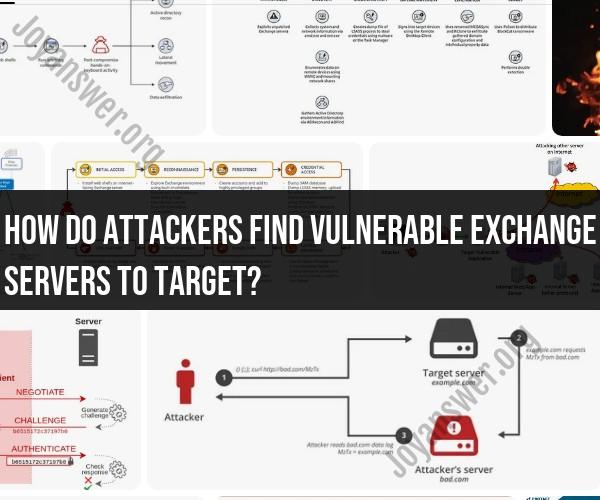
How do attackers find vulnerable Exchange servers to target?
Can an Insurance Company Deny a Claim?
Yes, insurance companies can deny insurance claims under certain circumstances. Insurance policies are legal contracts between the insurer and the policyholder, and they outline the terms and conditions under which claims will be paid. Insurance companies can deny a claim for various reasons, including:
Policy Exclusions: Insurance policies often have specific exclusions that list the situations or events not covered by the policy. If the cause of the claim falls under one of these exclusions, the claim may be denied.
Coverage Lapses: If the policyholder fails to pay premiums and the policy lapses, the insurance company has the right to deny claims during the period of the lapse.
Misrepresentation: If the policyholder provided false or incomplete information when applying for the policy, and this misrepresentation is discovered, the claim may be denied.
Non-Compliance: Failure to follow the terms and conditions of the policy, such as not taking required safety measures, may lead to claim denial.
Waiting Periods: Some policies have waiting periods before certain types of coverage become effective. Claims filed during this waiting period may be denied.
Coverage Limitations: Claims that exceed policy limits or sub-limits may not be fully paid, and the policyholder may be responsible for any amount over the limit.
Investigation Findings: If the insurance company's investigation reveals fraudulent activity or that the event in question didn't occur as claimed, the claim may be denied.
Late Notification: Many insurance policies require prompt notification of claims. Failing to report a claim within the specified time frame may result in a denial.
It's essential for policyholders to thoroughly understand their insurance policies and their rights and responsibilities. If a claim is denied, policyholders have the right to appeal the decision and work with the insurance company to resolve disputes. Additionally, consulting with legal counsel or an insurance expert may be advisable in cases of denied claims.
How Attackers Find Vulnerable Exchange Servers:
Attackers can find vulnerable Microsoft Exchange servers to target through various methods, and these methods often involve scanning the internet for specific vulnerabilities. Some common ways attackers identify vulnerable Exchange servers include:
Scanning Tools: Attackers use automated scanning tools to search for servers with open ports and specific services running, such as those associated with Microsoft Exchange.
Shodan and Censys: Search engines like Shodan and Censys index the internet and can reveal servers with open ports and services, including Exchange servers.
Exploit Databases: Attackers may consult exploit databases and forums where known vulnerabilities and exploits are shared and discussed.
Vulnerability Scanning: Attackers may use vulnerability scanners to identify known security flaws in Exchange servers, looking for unpatched systems.
Phishing and Social Engineering: In some cases, attackers may use phishing emails and social engineering to trick individuals within an organization into revealing information about their Exchange server or providing access to it.
Publicly Available Information: Some organizations inadvertently disclose information about their Exchange servers in publicly accessible documents, websites, or metadata.
Once attackers identify vulnerable Exchange servers, they can exploit the known vulnerabilities to gain unauthorized access, steal data, or perform other malicious activities. It's crucial for organizations to maintain a strong cybersecurity posture, including applying security patches, monitoring for suspicious activity, and employing security best practices to defend against such attacks.
Uncovering How Attackers Target Vulnerable Exchange Servers
Attackers target vulnerable Exchange servers by exploiting known vulnerabilities in the software. These vulnerabilities can be found in a variety of ways, including through public vulnerability databases, security advisories, and social engineering attacks.
Once an attacker has identified a vulnerable Exchange server, they can use a variety of tools and techniques to exploit the vulnerability and gain access to the server. Some common attack vectors include:
- Sending malicious emails: Attackers can send malicious emails to users of the Exchange server. These emails may contain links to malicious websites or attachments that exploit the vulnerability.
- Exploiting web applications: Attackers can exploit vulnerabilities in web applications that are running on the Exchange server.
- Exploiting remote desktop protocol (RDP): Attackers can exploit vulnerabilities in RDP to gain access to the Exchange server.
Exploiting Vulnerabilities in Exchange Servers: An Overview
When an attacker exploits a vulnerability in an Exchange server, they can gain access to the server and its data. This can include user accounts, email messages, and other sensitive information.
Attackers can use this information to steal data, launch further attacks against the organization, or extort money from the organization.
Protecting Exchange Servers and Mitigating Attacks
There are a number of things that organizations can do to protect their Exchange servers from attack and mitigate the impact of attacks. These include:
- Keeping Exchange servers up to date: Microsoft regularly releases security updates for Exchange server. Organizations should apply these updates as soon as possible to patch any known vulnerabilities.
- Using strong passwords: Organizations should require users to use strong passwords and enable multi-factor authentication (MFA) for all Exchange server accounts.
- Segmenting networks: Organizations should segment their networks so that attackers cannot easily move laterally from one server to another.
- Implementing security controls: Organizations should implement security controls such as firewalls, intrusion detection systems, and intrusion prevention systems to protect their Exchange servers from attack.
Steps to Enhance Exchange Server Security
In addition to the basic steps outlined above, organizations can also take the following steps to enhance Exchange server security:
- Implement role-based access control (RBAC): RBAC allows organizations to restrict access to Exchange servers and their data to only those users who need it.
- Disable unnecessary services: Organizations should disable any unnecessary services that are running on Exchange servers.
- Use a web application firewall (WAF): A WAF can help to protect Exchange servers from web-based attacks.
- Monitor Exchange servers for suspicious activity: Organizations should monitor their Exchange servers for suspicious activity and investigate any anomalies as soon as possible.
Staying Informed About Exchange Server Vulnerabilities
Organizations should stay informed about Exchange server vulnerabilities by subscribing to security advisories from Microsoft and other trusted sources. Organizations should also regularly scan their Exchange servers for vulnerabilities using a vulnerability scanner.
By following these steps, organizations can protect their Exchange servers from attack and mitigate the impact of attacks.
Additional tips for enhancing Exchange server security:
- Use strong encryption: Organizations should encrypt all sensitive data stored on Exchange servers.
- Implement a backup and recovery plan: Organizations should have a backup and recovery plan in place in case their Exchange servers are compromised.
- Educate users about security best practices: Organizations should educate users about security best practices, such as how to identify and avoid phishing emails.
By taking these steps, organizations can significantly reduce their risk of being attacked and minimize the impact of any attacks that do occur.